Secure OPS
Empower your security team with real-time alerts, automated threat detection, and streamlined compliance reporting—all within a flexible, scalable platform that adapts to your evolving infrastructure. Secure Ops is your next-gen SIEM for comprehensive, unified, and future-proof security management.
Key Features

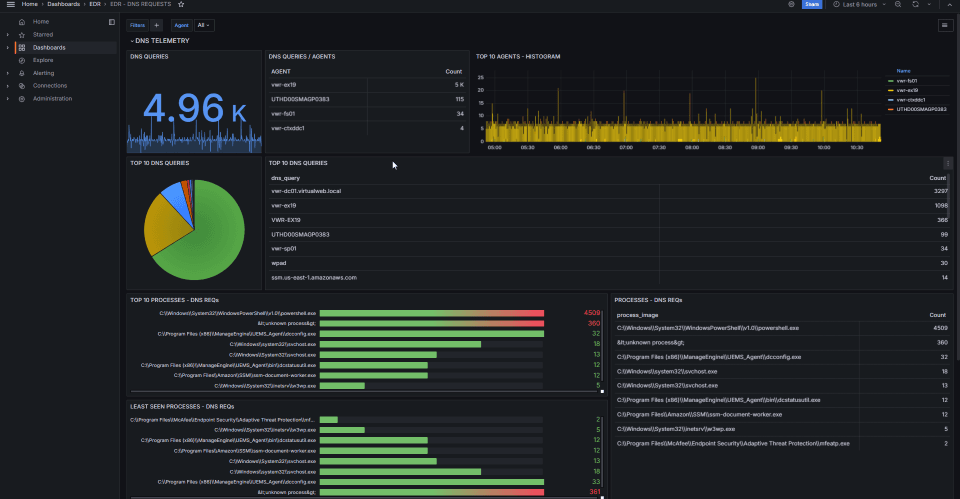
Data Collection & Ingestion
Log collection from operating systems, applications, and network devices
Event Processing
Real-time log parsing and normalization

Threat Detection
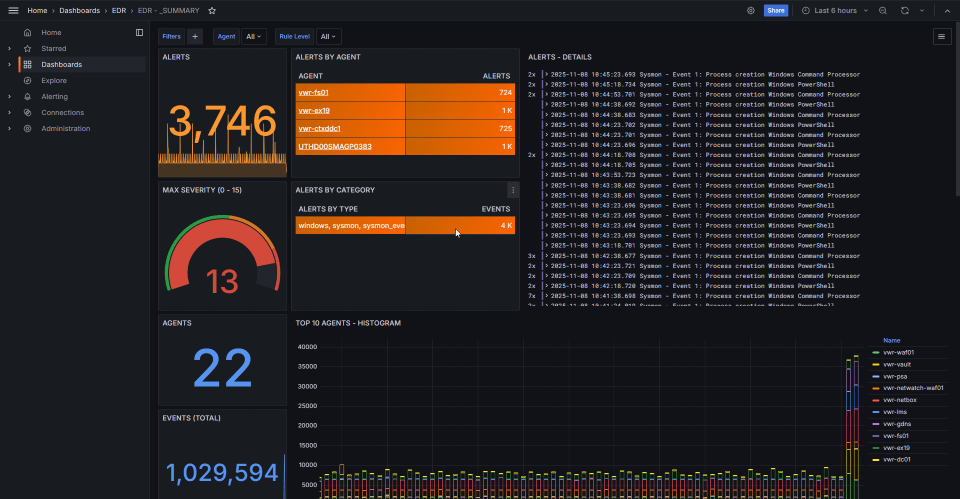
Machine learning-based behavioral analysis with over 3,000 prebuilt detection rules.

Compliance & Reporting
Automated compliance reporting and policy violation detection.
Secure Ops simplifies SIEM
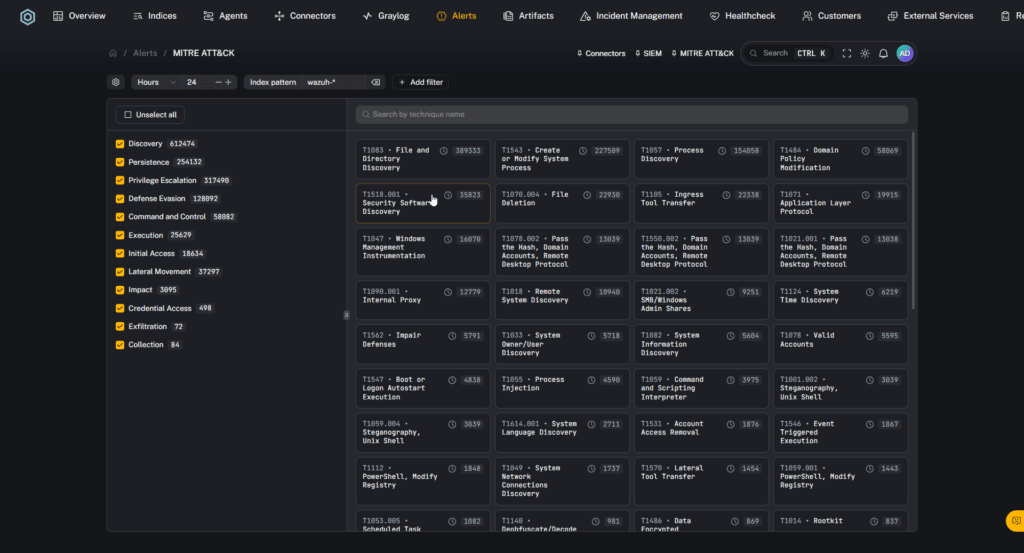
With robust support for multiple compliance frameworks, Secure Ops simplifies adherence to industry standards such as GDPR, HIPAA, PCI, NIST and more. Its advanced CVE update integration ensures your threat intelligence is always current, while built-in MITRE ATT&CK analysis offers in-depth insights into attack patterns and adversary tactics.
Empower your security team with real-time alerts, automated threat detection, and streamlined compliance reporting—all within a flexible, scalable platform that adapts to your evolving infrastructure. Secure Ops by Netwatch.ai is your ultimate partner for comprehensive, unified, and future-proof security management.
Key Features
Data collection & Ingestion
- Centralized log collection Easily collect data different Applications, Operating systems, Network Devices or cloud service providers.
- Syslog Server Receive real-time notifications with proactive information
- File Integrity Monitoring Compare against historical data to detect unauthorized changes
Event Processing & Normalization
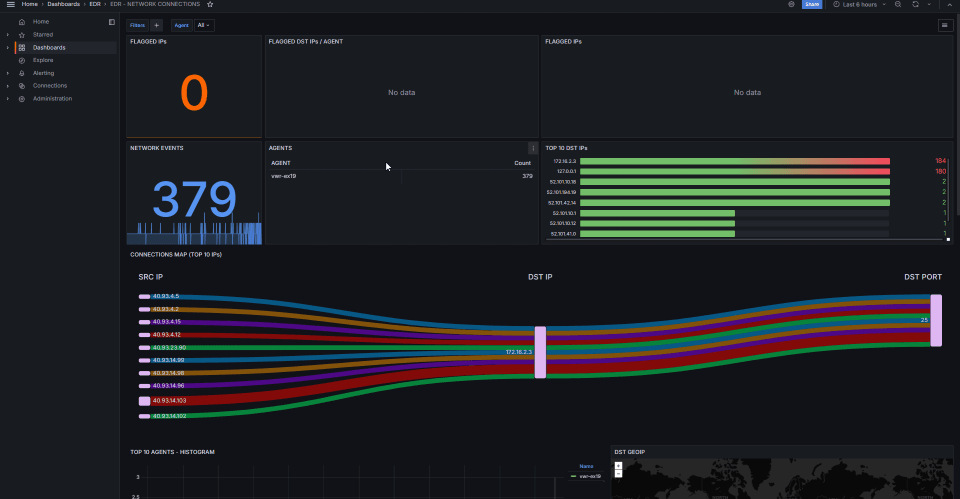
- Multi-Cloud Integration: Cross-source event correlation
- Unified Visibility: Custom decoders for diverse log formats
- Real-Time: Log parsing and data normalization

Threat Detection and Analytics
- Predictive Analytics: Utilize advanced anomaly detection through machine learning.
- Pre-built Detection Rules: Over 3,000 prebuilt rules or write custom rules for micro adjustments
- Full integration: Use threat feeds to enhance real time intelligence with CVE and MITRE ATT&CK databases
User-Friendly Interface
- Intuitive Dashboard: Enjoy a user-friendly interface that simplifies navigation and allows users to quickly access critical metrics and insights.
- Drill-Down Capabilities: Easily drill down into any expenditure category for a closer look at specific instances or compliance frameworks.
Compliance and Reporting
- Pre-built Dashboards: Complaince framwork dashboards for GDPR, PCI, NIST, HIPAA and others
- Compliance Reports: Generate compliance reports aligned with corporate policies or regulatory requirements to ensure accountability.
Benefits

Enhanced Security Control
Empower your security team with real-time alerts, automated threat detection, and streamlined compliance reporting—all within a flexible, scalable platform that adapts to your evolving infrastructure.

3rd Party Integrations
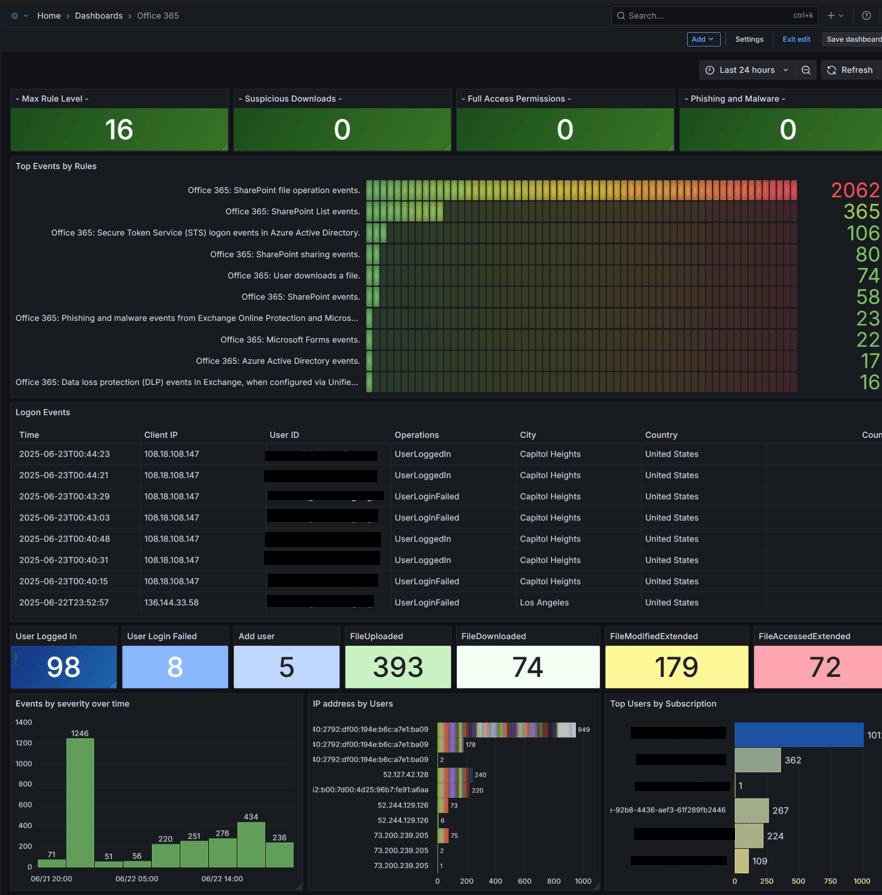
The platform supports integrations with various third-party security tools including Office365, Mimecast, Huntress, CarbonBlack, Crowdstrike, Darktrace, Bitdefender, and Defender for Endpoint, enabling comprehensive and unified security operations.
Incident Response Automation
includes automated actions such as blocking IPs and killing processes, intelligent alert prioritization and scoring, case management for tracking incidents, seamless API integrations with external security tools, and support for custom response scripts and playbooks.

Compliance Reporting
The Compliance & Reporting features offer pre-built dashboards for standards like PCI, CJIS, NIST, HIPAA, GDPR, CIS automated compliance reporting, audit trail management, policy violation detection, and secure archiving with historical data retention.
Use Cases

Startups
Quickly understand cloud costs as businesses scale and onboard new tools, facilitating budget management in rapid growth phases.

Enterprise Organizations
Monitor cloud expenses across a sprawling environment of services and applications, where visibility and control are critical.
IT Departments
Use for regular financial reviews to assess departmental spending and enforce budget limits more effectively.

